Workplace Monitoring: Boon or Bane?
Faculty Contributor : Rahul De, Professor
Student Contributors : Aishwarya A.
The advent of computers and the internet has drastically altered the way organizations work. Information technology is now the backbone of most successful organizations. The effectiveness of the information systems depends largely on its employees. Several issues arise due to misuse of information systems by employees. Organizations introduced workplace monitoring to ensure effective and efficient use of the organization’s information systems. However, workplace monitoring has raised serious concerns about employee privacy at the workplace. This article explores the practice of electronic workplace monitoring in India, the related human resource issues faced by the management in adopting these practices and the way forward for these organizations.
In the USA, nearly 77% of employers monitor their employees’ activities at the workplace1. The increased incidence of information systems misuse by employees explains the staggering figure. Inappropriate use of information systems leads to loss in employee productivity and exposure of the organization’s assets to cyber-attacks. This has necessitated the use of workplace monitoring tools by employers.
Monitoring practices may intrude upon an employee’s privacy, causing undue stress to the employees. The stress may lead to low employee productivity or worse, attrition. The challenge for the management is to ensure efficient use of the organization's information assets without compromising on employee privacy or losing talent to stress induced by the organization’s monitoring practices.
Workplace Monitoring in Organizations2
Every organization has a defined set of rules detailing the proper practices to be followed by employees in going about their daily business. This is popularly known as the Code of Conduct. Workplace monitoring essentially means observing any deviation in the employee’s activities from the organization’s Code of Conduct.
Workplace Monitoring Tools
Technology has made workplace monitoring easy. Some examples of e-workplace monitoring include performance tracking, internet usage monitoring, computer searches, telephone monitoring, video monitoring, email monitoring, keystroke monitoring, etc. Some of the popular tools available in the market are as shown below (Exhibit 1). One innovative product by SpectorSoft offers a video style playback tool that enables you to see what an employee does on the computer and internet.
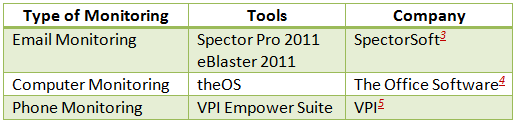 Exhibit 1 Popular Workplace Monitoring Tools
Exhibit 1 Popular Workplace Monitoring Tools
Workplace monitoring is more common in US and UK organizations. In India, organizations in the relatively new sectors such as IT, BPO and KPO have adopted workplace monitoring. This can be attributed to the heavy western influence on the corporate culture of IT, BPO and KPO organizations.
Rationale behind Workplace Monitoring
Most organizations rely on their information systems to run their business. They effectively and efficiently collect, store, process and communicate information in an organization. Organizations that successfully implement and manage their information systems have a clear competitive advantage and generate 40% more returns than their competitors6. Hence, organizations usually invest heavily in their information systems. As per a Gartner report7, worldwide IT spending will rise by 7.6% in 2011. The success of information systems in helping an organization achieve its objectives depends on its employees.
Productivity and Revenue Losses
With every employee equipped with either a laptop or desktop with access to the internet, it opens a window of opportunity for Cyberslacking. A mind-boggling number of applications ranging from online streaming players to interactive games are available to an employee now. According to an International Data Corporation survey8, 30-40% of web surfing by an employee is not work related. Shown below (Exhibit 2) is an example depicting productivity loss due to Cyberslacking by a senior software engineer.
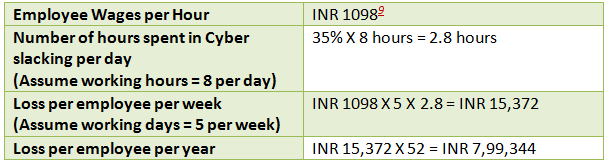 Exhibit 2 Employee Productivity Loss
Exhibit 2 Employee Productivity Loss
An organization incurs a loss of almost INR 8 Lakhs due to Cyberslacking by one employee. One can now compute the total loss to the organization due to Cyberslacking, which will be a very large amount. This necessitates monitoring of an employee’s activities by an organization.
Data Security Concerns
In India, data security is one of the top priorities for many organizations. According to the BPO knowledge base10, as of September 2004, almost 83% of BPO companies had reported a security breach. This is in contrast with the worldwide 64%. There are no stringent legal laws related to data security in India. While cyber laws are still in the nascent stage, cybercrimes are increasing exponentially. It has fallen upon the organization to guard its assets. According to the KPMG-DSCI survey (2010), almost 70% of the companies have admitted that major data security threats emerge internally11. Loss of confidential or sensitive information such as patents and customer information could cost a company heavily. The company will end up losing its business due to information leaks.
Most of the security threats are from inside the organization. The threats perpetuated by the employees could be intended or unintended. The intended threat, more commonly known as industrial espionage, poses a serious challenge to organizations. Current or former employees are responsible for almost 58% of industrial espionage. The unintended threats are a consequence of social engineering attacks which throw open the gates to confidential corporate information. In a social engineering attack, the attacker gets his task accomplished through the victim. Common threats like Trojan, virus, and malware can also result in loss of critical information. Workplace monitoring will keep a check on such activities whether intended or unintended.
Cannibalization of an Organization’s Resources
Employees often use the organization’s information systems for non-work related activities. Massive downloads eat into the bandwidth allotted for work-related activities. Downloading pirated software, music and movies using the company’s resources are yet another concern. Monitoring will help keep in check such activities, which cannibalizes the resources allocated for work related activities.
Legal Issues
Emails are monitored not only to check employee productivity but also to ensure they are compliant with the discrimination laws of the land. According to the Information Technology Act (2000) of India, sending threatening and defamatory emails is a crime12. The employer will be liable for sending such emails using the organization’s resources and will be subject to lawsuit for hosting a hostile work environment.A defamatory email sent by one employee could bring a lawsuit on the organization, tarnishing its brand image. It becomes important for management to ensure such untoward incidents do not occur.
Shown below (Exhibit 3) are commonly cited reasons by most organizations for introducing such practices in the workplace. These issues necessitate workplace monitoring in organizations to protect the misuse of information systems by its employees.
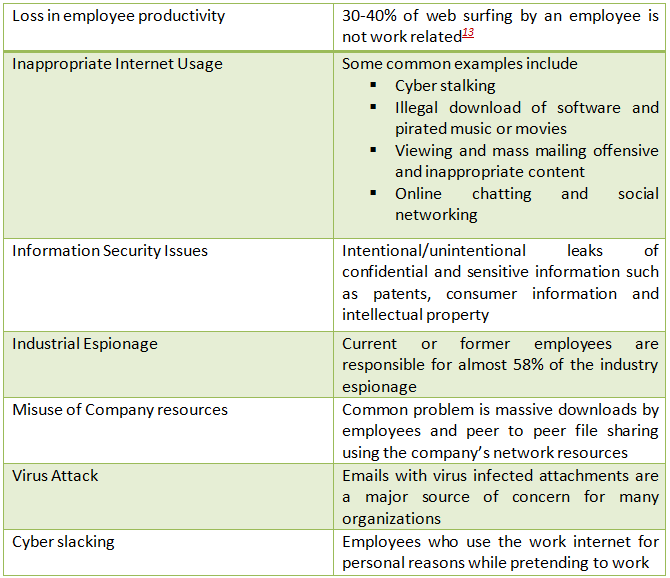 Exhibit 3 Common reasons cited by organizations for monitoring workplace
Exhibit 3 Common reasons cited by organizations for monitoring workplace
Employee Privacy Concerns
The most critical resource of any organization is its employees. An employee’s productivity is largely dependent on the work environment. A lot of thought is put into creating an environment conducive for working by the management. But the practice of workplace monitoring has raised serious privacy concerns among employees. The intrusion of the employee’s privacy will negatively affect the employer-employee relationship. The relationship is strained further when the employee is unaware that he is constantly monitored. Electronic surveillance will prove detrimental to an open culture built on trust, motivation and commitment.
Constant monitoring might place undue stress on an employee who will not perform at his best under stress. Hence, it becomes important for the management to ensure that the employee’s privacy rights are not infringed due to monitoring practices and employees are not placed under any form of stress.
There is no legislation in India which directly protects the employees’ privacy rights. Right to Privacy is implicitly included in the Fundamental Right to Life under Article 21 of the Constitution14. With the law limiting the employee’s privacy at the workplace, employees may get demotivated and choose to quit the company leading to attrition.
The organization stands to lose if good talent leaves the company due to unfavourable work conditions. Employers invest both time and money to attract the right talent to the company. Even more time and money is spent in training the employees and retaining them. It becomes the responsibility of the management to strike a fine balance between protecting its information systems and addressing its employees’ privacy concerns. This becomes all the more significant in today’s context as frequent job-hopping by employees is turning out to be a major problem in many organizations. Attrition is as high as 40% in BPO firms15.
The Way Ahead
Management needs to tread a fine line to protect its information systems and its employee’s rights. Management has to develop fair and concrete policies, which clearly outline the appropriate practices and procedures to be adopted at the workplace by employees. The policies and consequences of non-compliance with the policies should be clearly communicated to employeesby management. Any non-compliance should be dealt with appropriately after thorough investigation to prevent the recurrence of the incident. An open door policy must be evolved wherein employees should be able to voice privacy concerns to senior management without fear or inhibition.
Conclusion
Technology is a double-edged sword. It has completely changed the way businesses are run today. While it has helped to run the businesses more effectively and efficiently, it has also made available a plethora of opportunities to misuse it. To protect its information systems without infringing upon employee’s privacy and to create a work environment conducive for employees to perform at their best, it becomes important for the management to adopt fair and appropriate workplace monitoring practices.
Keywords
Information Technology, Workplace Monitoring, Information Systems, Employee Privacy concerns
Contributors
Rahul De is a Professor in the Area of Quantitative Methods & Information Systems at the IIMB. He holds a doctorate from J.M. Katz Graduate School of Business, University of Pittsburgh. He is reachable at
rahul@iimb.ernet.in. .
Aishwarya A (PGP 2010-12 at IIM Bangalore) holds a B.E from Madras Institute of Technology, Anna University. She is reachable at
aishwarya.a10@iimb.ernet.in. .
References
-
MSN Computing, 2009, “Monitoring at the Workplace”, Sept 4, http://computing.in.msn.com/article.aspx?cp-documentid=3209038, Last Accessed on Sept 21, 2011
-
Samantha, Lee, & Brian, H., Kleiner, 2003,Electronic Surveillance in the Workplace, Management Research News, http://www.emeraldinsight.com/journals.htm?articleid=866841 Last Accessed on Sept 27, 2011
-
SpectorSoft, http://www.spectorsoft.com/, Last Accessed on Sept 21, 2011
-
The Office Software, http://www.theofficesoftware.com/, Last Accessed on Sept 21, 2011
-
VPI, http://www.vpi-corp.com/, Last Accessed on Sept 21, 2011
-
Jeanne, W., Ross, & Peter, Weill, 2002, “3 Six IT Decisions your IT people should not make”, http://kenstott.com/Links/Six_IT_Decisions_Your_IT_People_Shouldnt_Make_HBR_OnPoint_Enhanced_Edition%5B1%5D.pdf, Last Accessed on Sept 26, 2011
-
IT Spending Forecast Summary, Q3 2011 Update, http://www.gartner.com/technology/research/quarterly-it-forecast/ , Last Accessed on Oct 30, 2011
-
The Importance of an Acceptable Use Policy, http://www.gfi.com/whitepapers/acceptable_use_policy.pdf , Last Accessed on Oct 30, 2011
-
Hourly Rate for Country: India, 2011, www.payscale.com/research/IN/Country=India/Hourly_Rate , Last Accessed on Sept 26, 2011
-
KnowledgeBase, www.bpoindia.org/knowledgeBase , Last Accessed on Sept 26, 2011
-
Sharma, Onkar, Indian BPOs Face Data Security and Privacy Challenges, http://dqindia.ciol.com/content/top_stories/2010/110122403.asp, Last Accessed on Sept 26,2011
-
Cyber Law of India: Introduction, www.cyberlawsindia.net/ , Last Accessed on Sept 26, 2011
-
Jeffrey, M., Stanton, & Kathryn, R., Stam, 2006, The Visible Employee: Using Workplace Monitoring
-
AzmulHaque, 2001, “India: Look Out! You are Being Watched At Work - E-Mail Monitoring And The Law Of Privacy”, www.mondaq.in/article.asp?articleid=30645 , Last Accessed on Sept 26, 2011
-
Attrition in Indian BPO Industry, www.bpoindia.org/research/attrition.shtml , Last Accessed on Sept 26,2011
